Many would agree that information is an attacker’s best friend when attempting to profile a target and gain information to formulate a more targeted attack. Recently, I’ve come across several Microsoft ClickOnce applications that have leaked an internal domain and username by default. This blog will show you how to remediate the default information leakage.
When deploying Microsoft ClickOnce applications, the Publishing Wizard within Visual Studio creates an Application Manifest file with information about the installation. The file is XML based and has an extension of .application. By default, Visual Studio creates a temporary certificate to sign the ClickOnce manifests and results in a file with contents similar to the following:
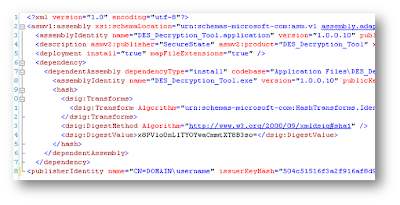
If you look at line 8, you will notice that the publisherIdentity reveals the sensitive information (<internal domain name>\<username>).
First, we must generate a new certificate that does not contain sensitive information in it to sign our manifests. This can be done using the makecert.exe tool within the .NET SDK. Additionally, we will use pvk2pfx.exe for certificate conversion. These tools are normally installed in C:\Program Files\Microsoft SDKs\Windows\v6.0A\bin\. Of course, the Visual Studio directory may have a different version for your installation. Screenshots of the two tools follow:

First we generate a certificate and provide a private key password using the following command:
The result should say “Succeeded” after supplying the passwords. The result should be the creation of MyKey.pvk and MyKey.cer files in the current working directory.
Next, we use the following command and password from the previous step to generate a .pfx (Personal Information Exchange) certificate file:
This step will have created the file MyPFX.pfx in your current working directory. This file can now be used to sign your manifests. To do this, open your project in Visual Studio and view the properties of it by selecting “
From here, choose the “Signing” tab on the left side of the properties page to see something similar to the following (notice the sensitive information shown by default):
Choose the “Select from File…” button on the right, and browse to your newly created MyPFX.pfx file.

Type in the password, and your project should now show your newly created signing information similar to the following:
Save your project, click on the “Publish” tab, and publish using the “Publish Wizard…” or “Publish” buttons. By following the above steps using your own digital certificate, your ClickOnce installation will no longer leak sensitive information by default.












No comments:
Post a Comment